SAML Authentication
This document outlines the process to register DeployGate as a SAML app. This operation requires “Administrator” privileges
Enterprise plans support user authentication using SAML (Security Assertion Markup Language). Using user account information already registered with a Project’s authentication provider (IdP: Identity Provider), Single Sign-On to DeployGate is available.
DeployGate is a SAML 2.0 compliant service provider (SP) and can be integrated with various authentication providers, including Google Workspace, OneLogin, and Microsoft Entra ID (Formally known as Azure AD).
This document outlines the steps to set up SAML authentication with the various authentication providers.
When enabling SAML authentication, all of the Workspace’s accounts will switch to a dedicated login screen for user authentication. Please note that this cannot be used in conjunction with Google Workspace authentication or standard DeployGate login methods.
Enabling SAML authentication
Both DeployGate and IdP must be properly configured to enable SAML authentication. Because the terminology for SAML authentication settings varies by the IdP, the following is a general overview of a typical process. Please make sure you read and understand the details of each IdP setting before proceeding with the configuration. We have specific configuration instructions for major IdPs, including Google Workspace and Microsoft Entra ID, so please refer to those documents for more details.
To enable SAML authentication, open the Workspace Admin Console’s settings page. Then, select “Authentication” from the left menu and select Enable SAML authentication from the SAML Authentication section.
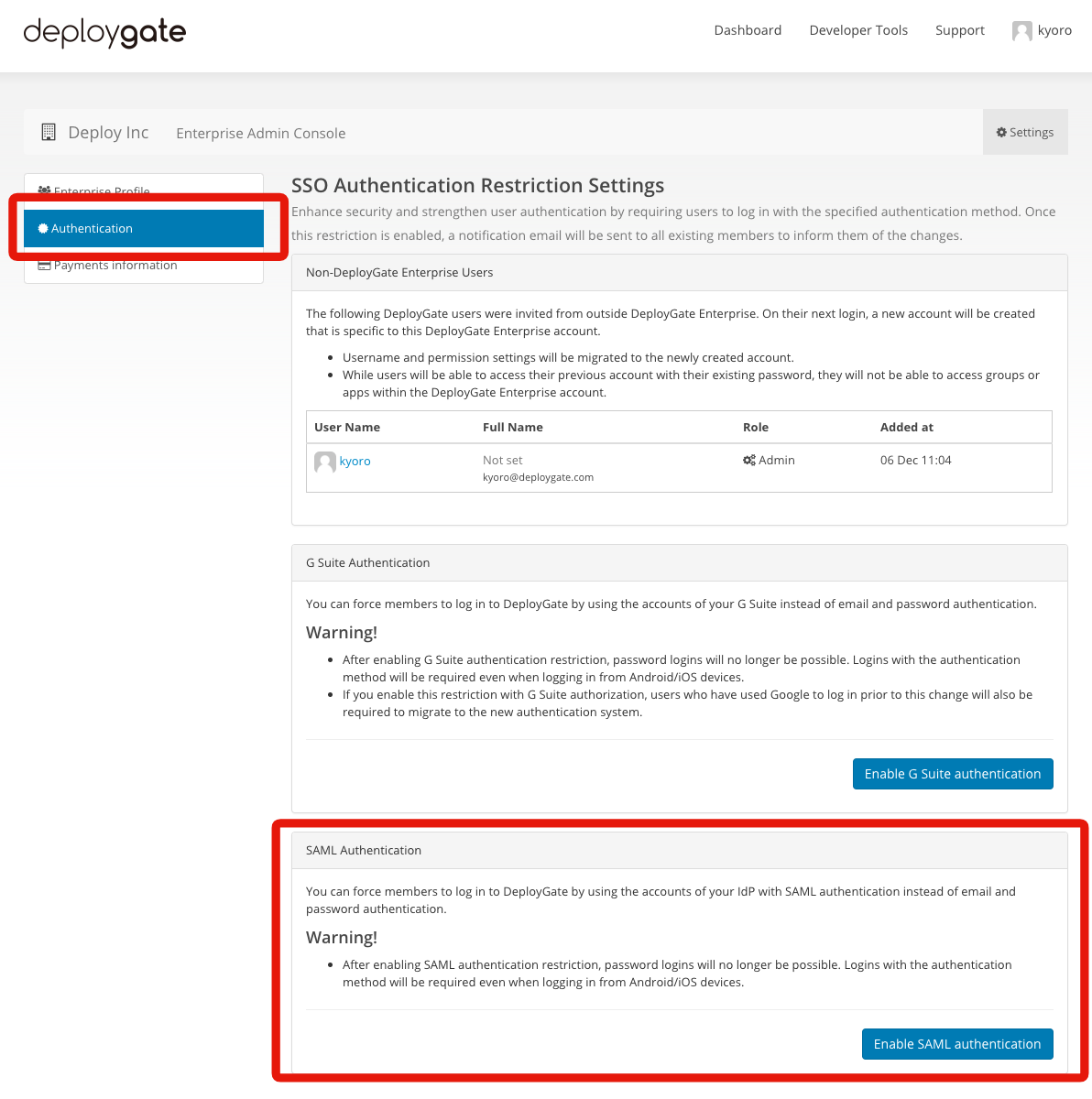
A settings wizard will appear and will guide you through the set up process, so enter the information required for SAML authentication into the form.
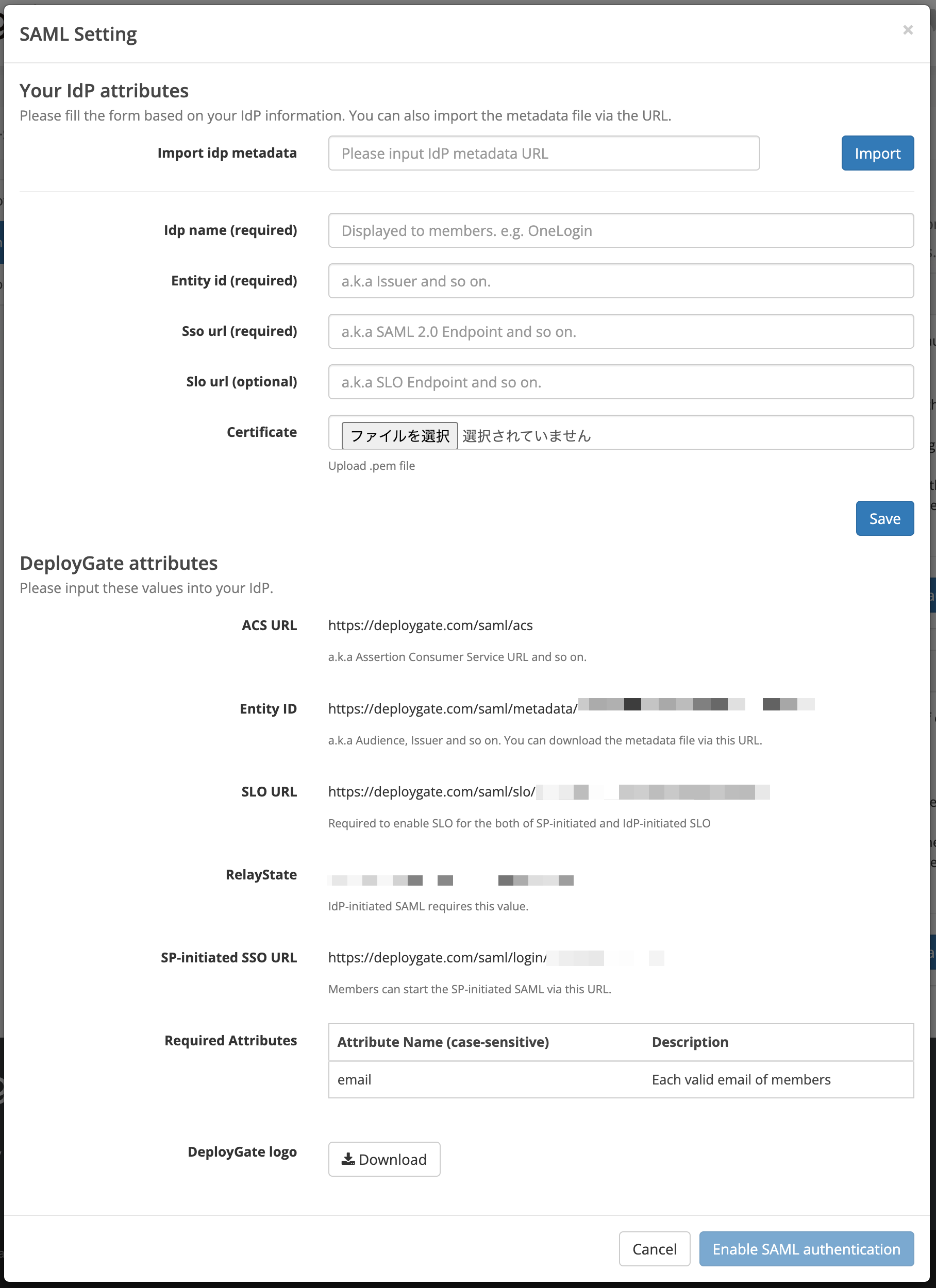
In the Your IdP Settings section, enter the IdP’s information to proceed with the integration with DeployGate. The information in this section is unique to each IdP and is typically provided by the IdP. This information is displayed when adding an SAML app in Google Workspace or when registering an app in OneLogin. (For details, please see the specific tutorials)
| Settings | Description |
|---|---|
| IdP Name | The name of the authentication provider that is displayed to members. The name can be anything, so we suggest a clear and descriptive name. It can be a service provider, such as OneLogin or Google Workspace, or “XX Company’s Google Workspace account.” |
| IdP Entity ID | The Entity ID provided by the IdP. The IdP typically provides this as part of the SP’s settings information. |
| SSO (Single Sign-On) URL | The URL for the IdP’s login screen. The IdP typically provides this as part of the SP’s settings information. |
| SLO (Single Logout) URL | The URL required to terminate IdP login sessions with SP-initiated SLO. The IdP typically provides this as part of the SP’s settings information. |
| IdP Certificate | The certificate that validates communication between the IdP and SP. Please use a X.509 format PEM file prepared by the IdP. |
It’s also possible to autofill the fields by Importing a metadata file (XML). Please note that this overwrites manual entries. To save the settings, select the save button (for manual entries) or the import button (for imports).
The bottom of the screen will display DeployGate’s information, which is required for the IdP’s settings. Please configure the IdP settings with this information to complete the process.
| Settings | Description |
|---|---|
| ACS URL | The ACS (Access Control) URL provided by DeployGate. |
| SLO URL | Unique ID that identifies DeployGate as an SP entity. This is equivalent to the download URL of DeployGate’s SP metadata file (XML). |
| SLO URL | The URL required to process logouts when using SP-initiated SLO or IdP-initiated SLO. |
| RelayState | The value for IdP-initiated authentication. If this is not specified on the IdP side, only SP-initiated authentication will function. |
| SP-initiated SSO URL | DeployGate’s dedicated login URL for the Workspace. |
| Required Attributes | The names and values of the attributes required for authentication between the IdP and DeployGate. These attributes are required. If they are not provided, we do not guarantee any functionality and cannot provide support for operational issues. |
| DeployGate Logo | DeployGate’s logo image. You can use this logo when registering DeployGate as an SAML app with the IdP. |
Please select urn:oasis:names:tc:SAML:2.0:nameid-format:persistent. It will not function properly with other formats.
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress URI is also available instead of email attribute.
Please use the logo image as an icon in the IdP settings. The SP-initiated SSO URL is the URL of the page where members log in. Please share it with members as needed.
After configuring the IdP, clicking on “Enable SAML authentication” will redirect you to the IdP login screen. If the login is successful, you should be redirected to DeployGate. If you see a message that states the authentication was successful, the SAML authentication process is completed.
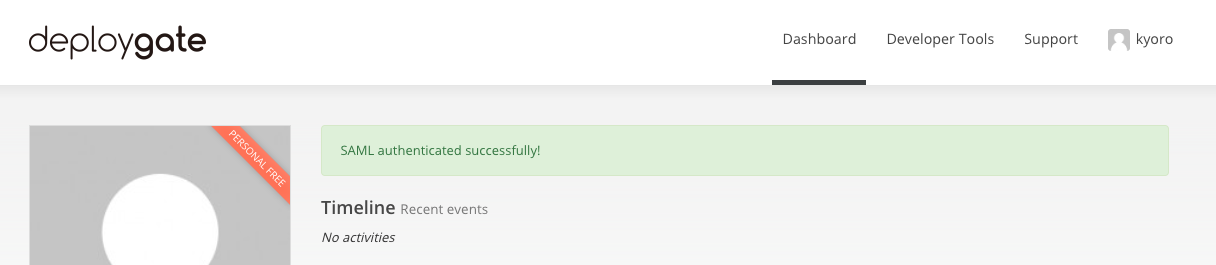
The 14 days after enabling SAML authentication is a transition period, and passwords can also be used to log in during this time. However, even during this transition period, SAML SSO will take precedence for users who have enabled SAML integration for their account, and their passwords will be disabled.
Dedicated Workspace Login Page
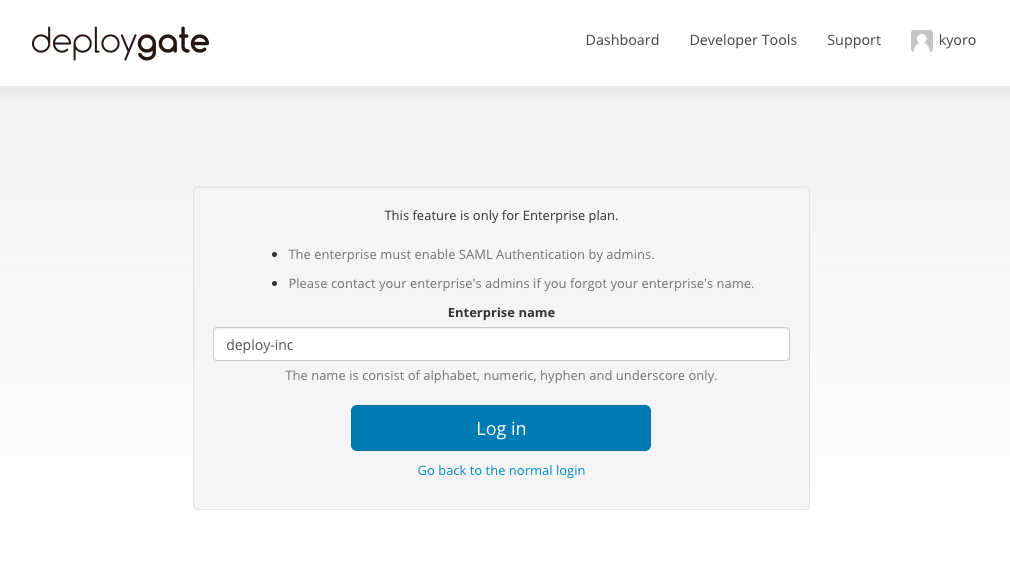
After enabling SAML authentication, a Workspace will have a dedicated login page to log in to DeployGate. Please use the “SP-initiated SSO URL,” which is displayed during the SAML setup process on the DeployGate Settings page.
In most cases, the URL will be https: /deploygate.com/saml/login/[Workspace name].
Emergency Use: Password authenticated logins for accounts with Administrator privileges
When a Workspace enables SAML authentication, the login authentication method will switch to SSO authentication via IdP for all Workspace users. Logging in with a password will no longer be possible. However, as an exception, accounts with administrator privileges will retain the ability to log in with passwords even after enabling SAML authentication. This is to ensure that key personnel can address IdP connectivity errors, configuration problems, or other issues that may require immediate attention. As such, please be mindful of managing administrator accounts. Only grant administrator privileges to necessary personnel and ensure that passwords are properly managed and protected.
Logging in with a password after enabling SAML authentication
To log in using a password after SAML authentication has been enabled, follow these steps:
- Log out of DeployGate.
- Reset your password using the password reset feature.
- Log in with your new password.
Only use password logins in an emergency. For all other times, use SSO authentication with the IdP. Also, please ensure that administrator accounts have strong passwords.
Depending on the conditions under which SAML was enabled, such as if the account has been separated into an Workspace-only account, you may be unable to reset your password using the standard interface. In such cases, you will see an error message instructing you to contact user support. We apologize for the inconvenience, but please contact user support for assistance.